
by WK Wallace | Jun 13, 2019 | Azure Server, Email, Security, Services
The instructions found on their website for setting up Proofpoint Essentials and connecting to Azure needs updating. Microsoft no longer allows users to access the “App Registration (legacy)” in order to get a KEY without a special character that isn’t supported by Proofpoint. You may have to generate dozens of keys to get one that Proofpoint will accept. Microsoft has also changed the name from Azure Active Directory to Microsoft Graph for setting domain read permissions.

by WK Wallace | Jul 21, 2010 | 2003/2008 Server, Windows 7, Windows Vista, Windows XP
For some printer models, the manufacturer does not package the drivers so that they can be installed as Additional Drivers on a print server. This is the case for many of the less expensive bubble jet, inkjet and multi-function (e.g. scanner/fax/printer) models. The manufacturers deem these to be “personal” printers for use only on the computer to which they are physically connected (parallel, USB or serial port). The manufacturer often says that printing over the network is “not supported” for these models.
If you attempt to install the drivers for these models as Additional Drivers (see for example Install Additional Driver on older OS), you will get some kind of an error or a request for the driver that can not be satisfied no matter what you do. You may also get an error message stating that there is a policy in effect that doesn’t allow NT4 drivers to be installed.
Unfortunately, there are some models that can not be used over the network because the print device and printer driver have to be in bi-directional communication throughout the printing process. The manufacturer’s documentation does not always make this requirement apparent, although there may be FAQs or other documents on the manufacturer’s web site that state this.
Except for those models discussed in the previous paragraph, you can bypass this problem by adding the printer as a local printer on the client computer and associating the printer with a network printer port (i.e. re-direct it to the printer share on the print server). No harm will be done by trying this approach if it doesn’t work, so it’s usually worth a try.
Here’s how to install a printer locally and re-direct it to a network printer port. These instructions are written for Windows XP. This technique does work with Windows 7, Vista, 2008, and 2003 but the dialogs are a bit different, so you may have to read between the lines.
- Logon at the client computer with a user account that has administrative rights and permissions on the client computer.
- Click Start, Printers and Faxes
- Right click in an empty space in the right pane and select Add Printer
- Click Next
- Select the Local Printer… radio button, remove the check mark from Automatically detect and install my Plug and Play printer; click Next
- Select the Create a new port: radio button; from the Type of port: drop down list, select Local Port; click Next
- In the Enter a port name: text box, key exactly the UNC name of the network printer (e.g. \\printservername\printersharename); click OK
- Selecting the appropriate entries from the Manufacturer and Printers columns or click the Have Disk button as appropriate
- Follow through the rest of the Add Printer wizard.

by WK Wallace | Mar 9, 2010 | Azure Server, Windows Server
Put simply, Windows Azure is the Windows Server operating system redesigned as a cloud-based service. At a very high level, Windows Azure is much like Windows Server, except that it’s hosted by Microsoft at its datacenters and not on-premise at your own company. That is, it provides a platform on which developers can create hosted applications and companies can run hosted applications and store data in the cloud.
But Windows Azure is not simply the current version of Windows Server modified to work in the cloud. Yes, Microsoft did of course start with a Windows Server core to create Windows Azure, but the system was also designed from the start to work as a cloud-hosted service. As such, Windows Azure and Windows Server both have capabilities that are unique to one that are not available in the other. According to Microsoft, the company will continue developing each product separately, all while bringing the respective capabilities of each system closer together. That said, because of their unique focuses, it’s likely that they will never truly mirror each other fully.
Another important aspect of Windows Azure is that it works within Microsoft’s notion of a hybrid computing model, allowing companies to utilize on premise servers for those tasks that need to be hosted onsite and cloud-hosted services that do not. So your company may choose to host some of its applications and data in the cloud but retain other on premise applications and data as needed. This system can also be utilized to slowly move resources to the cloud over time as you evaluate the cost, effectiveness, and convenience of such a strategy.
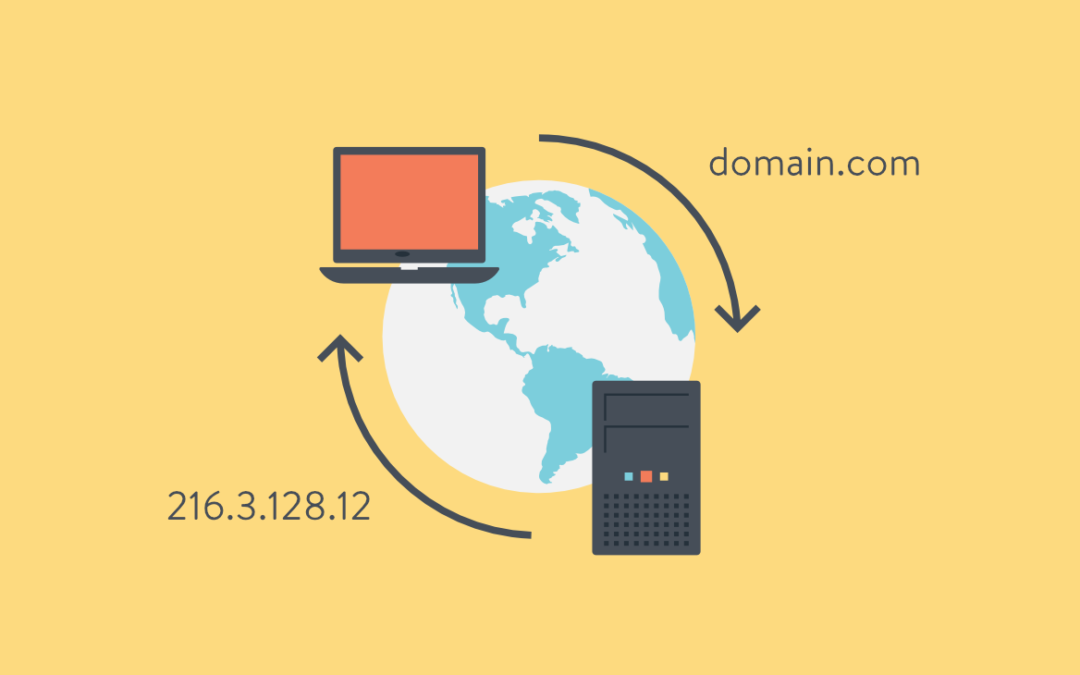
by WK Wallace | Feb 15, 2010 | Networking, Windows Server
How DNS should be configured? In a Windows Server environment, DNS is configured incorrectly more often than you’d think. After installing the DNS service on a server, that server must (there are a few uncommon instances where this might not be true) use its own IP or localhost for DNS resolution. Most of the time, here’s what I see. Upon opening the network connection tcp properties, DNS is set to that organization’s ISP DNS settings. Maybe sometimes, localhost in primary and an ISP DNS in the secondary. When you think about it logically:
- You just installed a DNS service, why would you need to outsource it?
- Do you really think your ISP cares what you name your internal systems?
- If they did, would you want them to know?
ISP DNS should never be used as an internal resolution source. That’s why your network is “private”. ISP DNS should be setup as DNS Fowarders. This means, if you browse to www.google.com on a workstation, the workstation should only query your internal DNS. When your DNS server browses its own DNS records and does not find an entry for www.google.com, it should then look to its forwarders for an answer. Your ISP should know this name, if it doesn’t, it will forward it to its forwards. So on and so forth. This is the order of DNS and should always be followed, unless you like seeing red marks in your event logs.




