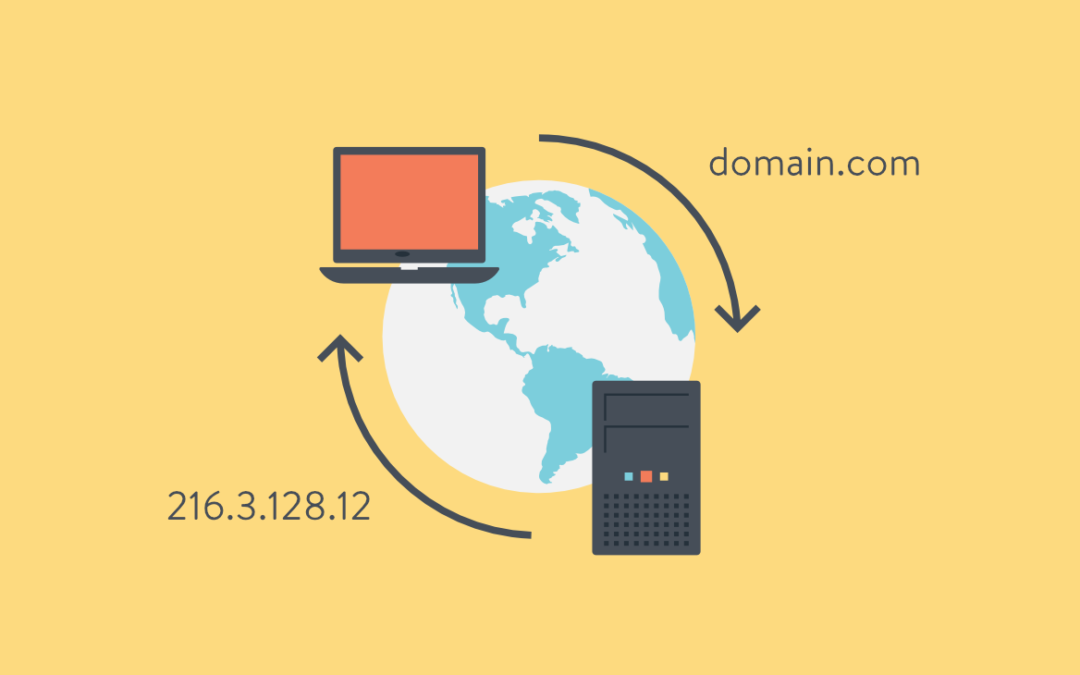
DNS – the root of all evil or an angel in disguise
How DNS should be configured? In a Windows Server environment, DNS is configured incorrectly more often than you’d think. After installing the DNS service on a server, that server must (there are a few uncommon instances where this might not be true) use its own IP or localhost for DNS resolution. Most of the time, here’s what I see. Upon opening the network connection tcp properties, DNS is set to that organization’s ISP DNS settings. Maybe sometimes, localhost in primary and an ISP DNS in the secondary. When you think about it logically:
- You just installed a DNS service, why would you need to outsource it?
- Do you really think your ISP cares what you name your internal systems?
- If they did, would you want them to know?
ISP DNS should never be used as an internal resolution source. That’s why your network is “private”. ISP DNS should be setup as DNS Fowarders. This means, if you browse to www.google.com on a workstation, the workstation should only query your internal DNS. When your DNS server browses its own DNS records and does not find an entry for www.google.com, it should then look to its forwarders for an answer. Your ISP should know this name, if it doesn’t, it will forward it to its forwards. So on and so forth. This is the order of DNS and should always be followed, unless you like seeing red marks in your event logs.
